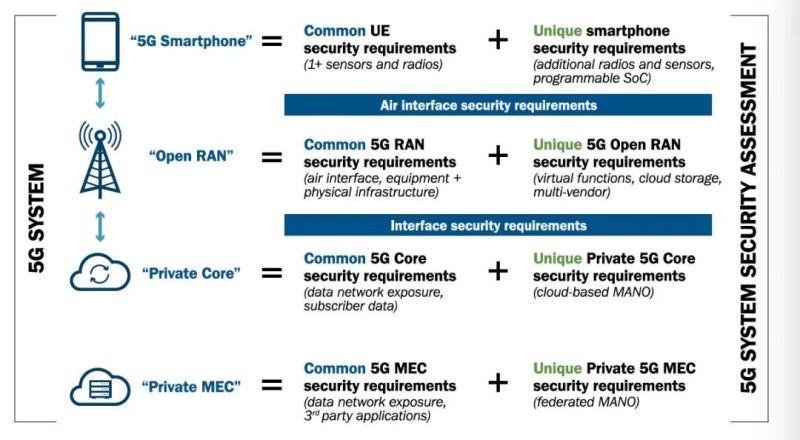
**5G (NR) Systems and Networks**
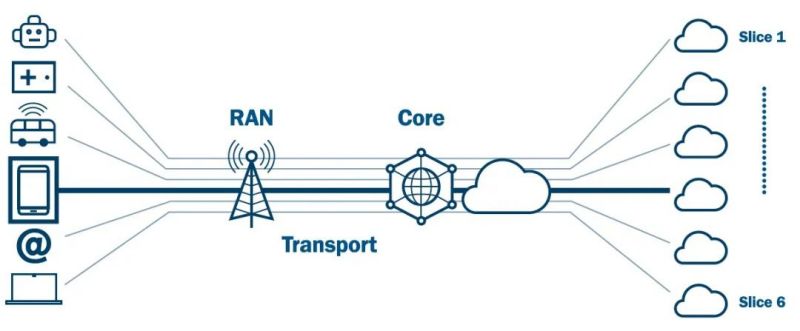
5G technology adopts a more flexible and modular architecture than previous cellular network generations, allowing greater customization and optimization of network services and functions. 5G systems consist of three key components: the **RAN** (Radio Access Network), the **CN** (Core Network) and Edge Networks.
- The **RAN** connects mobile devices (UEs) to the core network through various wireless technologies like mmWave, Massive MIMO, and beamforming.
- The **Core Network (CN)** provides key control and management functions like authentication, mobility, and routing.
- **Edge Networks** allow network resources to be located closer to users and devices, enabling low-latency and high-bandwidth services like cloud computing, AI, and IoT.
5G (NR) systems have two architectures: **NSA** (Non-Standalone) and **SA** (Standalone):
- **NSA** utilizes existing 4G LTE infrastructure (eNB and EPC) as well as new 5G nodes (gNB), leveraging 4G core network for control functions. This facilitates faster 5G deployment building on existing networks.
- **SA** has a pure 5G structure with brand new 5G core network and base station sites (gNB) delivering complete 5G capabilities like lower latency and network slicing. The key differences between NSA and SA are in core network dependence and evolutionary path – NSA is a baseline for the more advanced, standalone SA architecture.
**Security Threats and Challenges**
Due to increased complexity, diversity and interconnectivity, 5G technologies introduce new security threats and challenges to wireless networks. For instance, more network elements, interfaces and protocols could be exploited by malicious actors like hackers or cybercriminals. Such parties frequently attempt to collect and process increasing amounts of personal and sensitive data from users and devices for legitimate or illegitimate purposes. Moreover, 5G networks operate in a more dynamic environment, potentially causing regulatory and compliance issues for mobile operators, service providers and users as they must adhere to varying data protection laws across countries and industry-specific network security standards.
**Solutions and Countermeasures**
5G provides enhanced security and privacy through new solutions like stronger encryption and authentication, edge computing and blockchain, AI and machine learning. 5G employs a novel encryption algorithm called **5G AKA** based on elliptic curve cryptography, delivering superior security guarantees. Additionally, 5G leverages a new authentication framework called **5G SEAF** based on network slicing. Edge computing allows data to be processed and stored at the network edge, reducing latency, bandwidth and energy consumption. Blockchains create and manage distributed, decentralized ledgers recording and validating network transaction events. AI and machine learning analyze and predict network patterns and anomalies to detect attacks/events and generate/safeguard network data and identities.
Chengdu Concept Microwave Technology CO.,Ltd is a professional manufacturer of the 5G/6G RF components in China , including the RF lowpass filter , highpass filter , bandpass filter , notch filter/band stop filter , duplexer,Power divider and directional coupler . All of them can be customized according to your requrements .
Welcome to our web : www.concept-mw.com or reach us at: sales@concept-mw.com
Post time: Jan-16-2024